PSA: Supply Chain Phishing (Using OneNote, OneDrive and SharePoint) – What You Need to Know
Source: NSB Cyber
Since 2023, there has been a re-surging supply chain phishing campaign exploiting Microsoft's trusted platforms—OneNote, SharePoint, and OneDrive—to bypass traditional email security filters and compromise organisations through trusted channels. These attacks are particularly difficult to detect and can spread rapidly because they use familiar Microsoft platforms and compromised internal accounts.
What’s Happening?
It all starts with a threat actor compromising one company's email account and quickly spirals from there. After establishing their foothold and performing quick reconnaissance on the user account they've compromised (e.g. getting an idea of what the user's role is in the company, what juicy access they have or sensitive information they hold), a threat actor may then send further phishing emails to colleagues, clients, and partners. Their objective is to keep daisy chaining their attack from user to user, organisation to organisation, until they hit the jackpot with an account they can do some real damage with!
What makes their attacks especially effective is this. Instead of attaching suspicious files, threat actors share links to malicious OneNote documents hosted on SharePoint or OneDrive.
Because these links point to trusted Microsoft domains, they often bypass email security filters and appear safe to recipients. The added complexity is, when you see an email from your boss, coworker, or client, you naturally trust it more and click without thinking twice.
The OneNote files are cleverly disguised, posing as invoices, contracts, or internal documents. Inside, they contain embedded links or fake login prompts designed to steal credentials or deliver malware.
Source: NSB Cyber
Attack Chain Breakdown
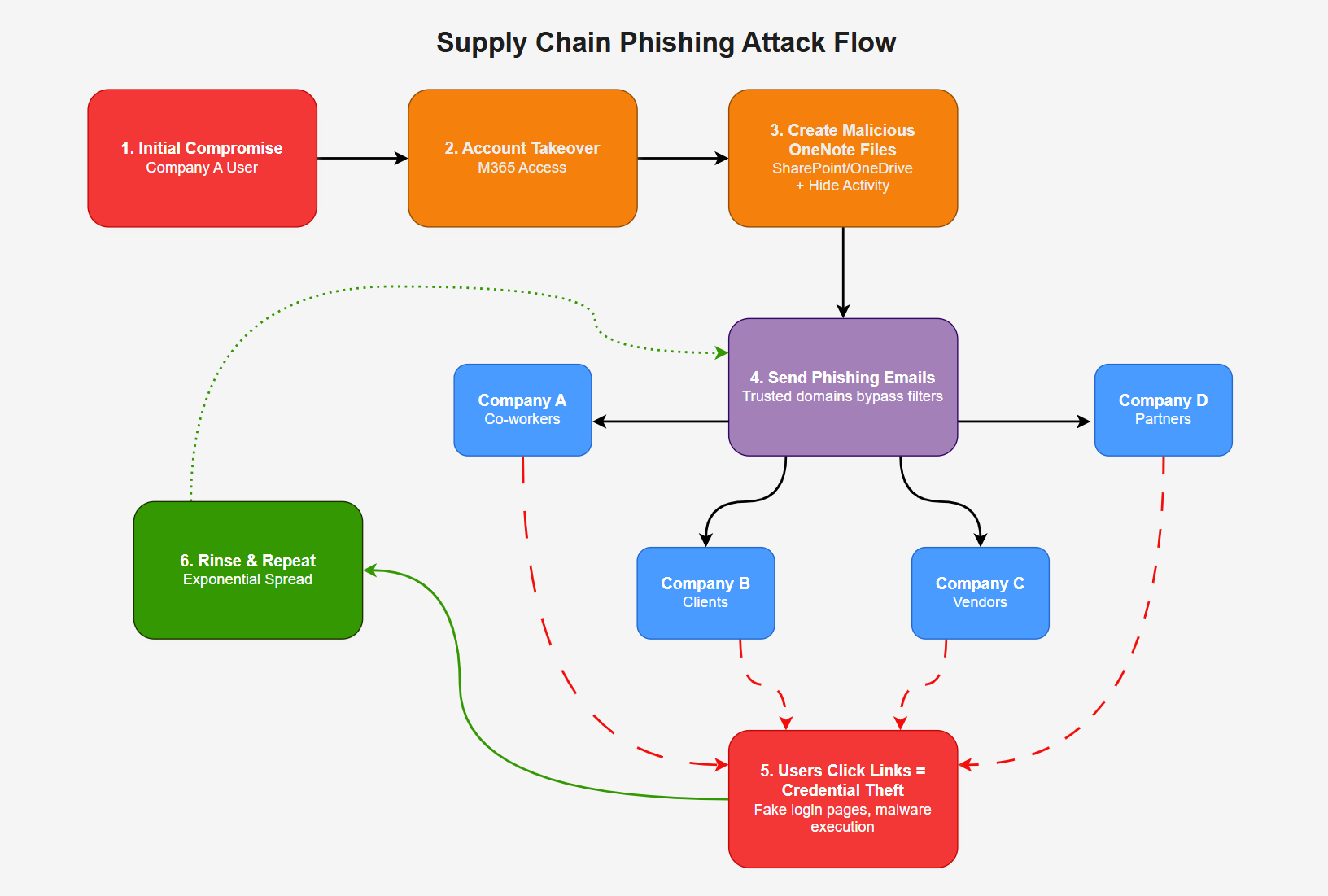
Here’s how the attack typically unfolds:
1. Initial Compromise - A legitimate business email account is compromised via credential theft or malware.
2. Account Takeover - Attackers gain full access to their M365 account, including SharePoint, OneDrive, and Teams, enabling lateral movement and further exploitation.
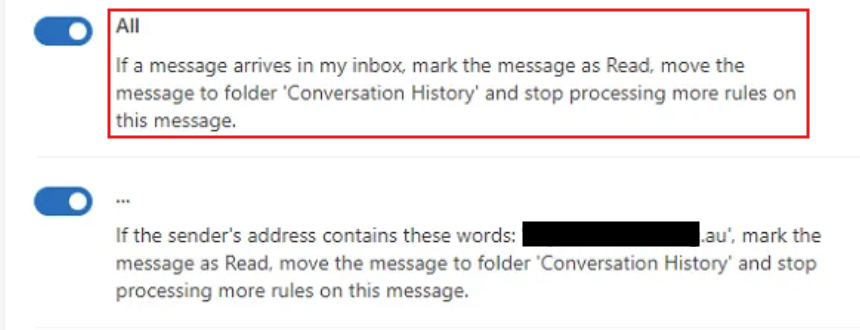
3. Covering Their Tracks - Attackers often establish email forwarding rules to redirect replies to their own accounts and create inbox rules to hide malicious activity from the compromised user.
Source: NSB Cyber
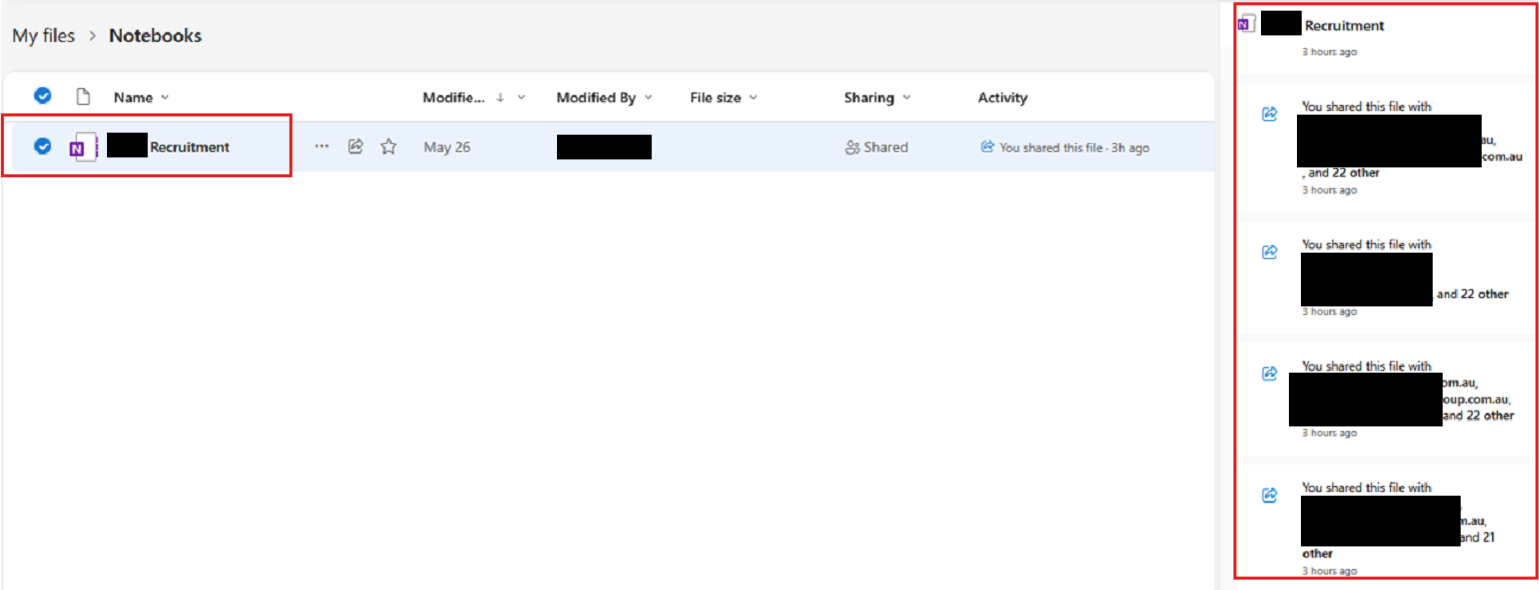
4. Malicious Content Creation - Attackers upload malicious OneNote files to SharePoint or OneDrive to launch phishing campaigns.
Source: NSB Cyber
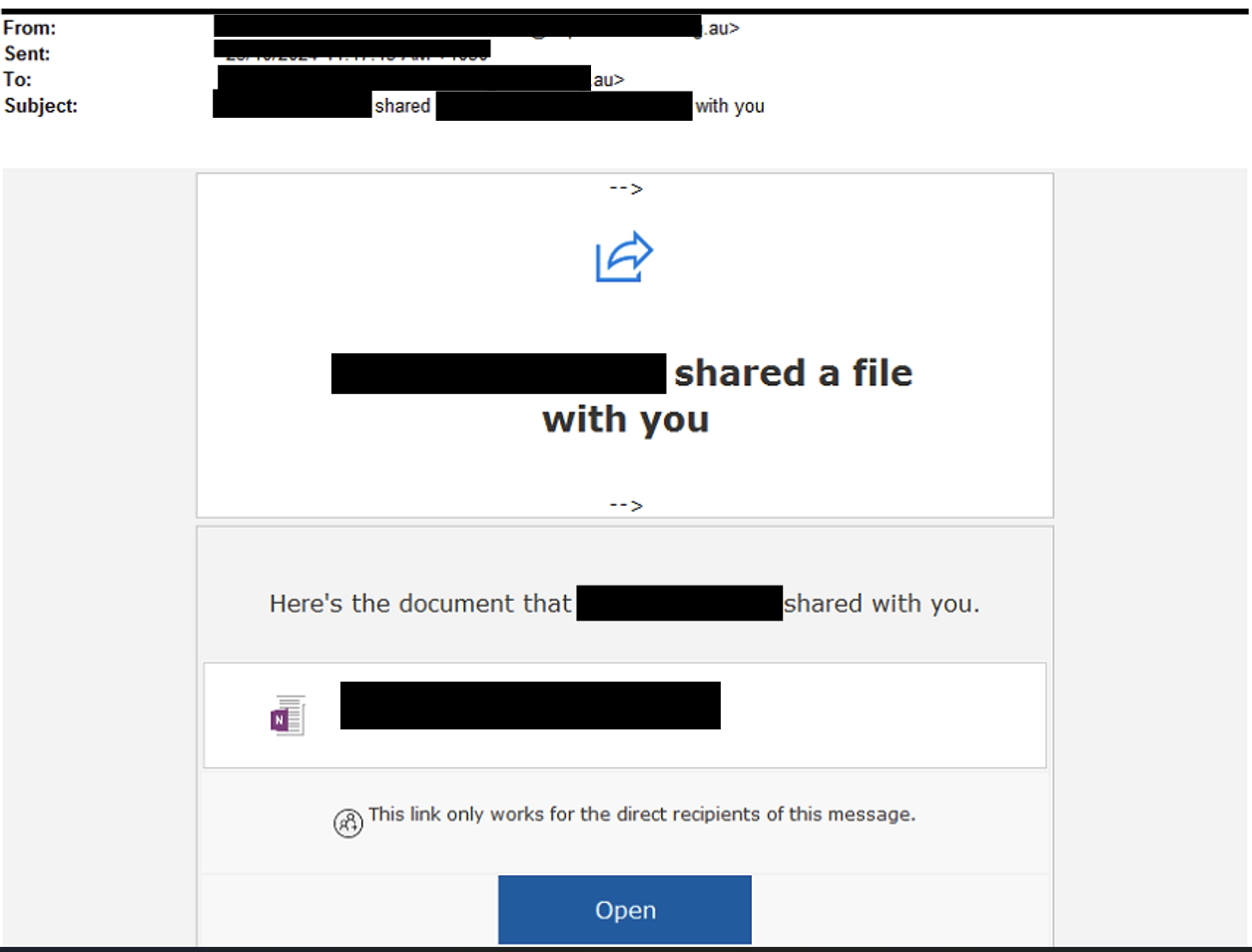
5. Internal Spread - The attacker shares links to the malicious OneNote file via email from the compromised user account.
Source: NSB Cyber
6. Recipient Clicks the Link - The OneNote file is legitimately hosted in SharePoint but contains embedded malicious links or scripts.
Source: NSB Cyber
7. Credential Harvesting or Malware Execution - Clicking embedded content redirects users to a fake Microsoft login page or triggers malware to download.
8. Rinse and Repeat - Each newly compromised account becomes a launchpad for further attacks, enabling exponential spread across tenants and organisations.
How to Protect Yourself
Individuals:
Pause before clicking - Even if an email looks like it’s from someone you know, take a moment to think.
Hover over links - Always check where a link is really going before clicking.
Verify urgent requests – Use a different communication channel (e.g., phone, text) to confirm the request is legitimate.
Check the URL - When you see a Microsoft login page, always look at the address bar. If it doesn’t start with a trusted Microsoft domain, don’t enter your credentials.
Be cautious with third-party logins - Ask yourself: Should I really be signing into a third-party site using my company’s Microsoft 365 credentials?
Trust your instincts - If something feels off or doesn’t look right, it probably is.
Business Owners and IT Teams:
Require Multi-Factor Authentication (MFA) for all users - No exceptions.
Invest in ongoing security training - Teach employees how to spot phishing and social engineering.
Enable Microsoft Defender for Office 365 – If you have the licensing, enable Safe Links, Safe Attachments, and anti-phishing policies.
Monitor for suspicious activity – Look for unusual login locations, external OneNote access, and inbox rule changes.
Set up security alerts – For new inbox rules, forwarding rules, and impossible travel.
Regularly audit M365 configurations – Harden your environment against common attack vectors such as sharing permissions and conditional access policies.
Optimise security tools - If you're using Microsoft Defender or Sentinel, make sure DeviceEvents, DeviceBehavior, and DeviceBehaviorEntities are enabled and collecting data.
If You’ve Been Compromised
Individuals:
Change your password immediately - Start with your M365 account.
Notify your IT/security team - Don’t try to handle it alone even if you are unsure.
Check for unauthorised inbox rules - Look for rules that forward or hide emails.
Review recent sign-ins - In My Sign-Ins Look for unfamiliar locations or devices.
Monitor your accounts - Watch for suspicious activity over the next few weeks.
Call in the professionals - If you’re unsure what to do, escalate. It’s better to overreact than under-respond.
Incident Responders:
Disable or lock the compromised account - Immediately.
Force a password reset - And ensure MFA is enabled.
Revoke all active sessions and refresh tokens - Cut off the attacker’s access.
Check for malicious inbox rules - Investigate if forwarding rules were added and remove them.
Audit email activity - Identify who was contacted and what was sent.
Search for malicious files - In SharePoint, OneDrive, and Teams.
Check for new enterprise apps or permissions - Attackers may have added malicious OAuth apps.
Communicate with affected users - Let them know what happened and what to watch for.
Document everything - For internal review and potential legal or insurance follow-up.
Engage external experts if needed - If the scope is unclear or the environment is complex, bring in professional incident responders.
The Bigger Picture
This phishing campaign works because it exploits trust—trust in Microsoft tools, trust in emails from colleagues, and trust in platforms we use daily. That's precisely what makes this campaign so dangerous.
However, with proper awareness, tools, and policies in place, these attacks can be effectively countered.
Whether you're safeguarding personal data or protecting an entire organisation, vigilance is essential. Implement multiple security layers and never assume a link is safe simply because it appears to come from Microsoft.
Ready to be supported by an experienced cybersecurity team? Let’s start the conversation - Book a meeting with us today.