#NSBCS.106 - The Fusion of Cyber and Kinetic Operations in Operation Absolute Resolve: US Hybrid Warfare
Absolute Resolve: The Integration of Cyber and Kinetic Warfare
The beginning of 2026 marked a dramatic turning point in Venezuela's long-standing political turmoil. On January 3 2026, the United States launched Operation Absolute Resolve, a large-scale military intervention that combined precision kinetic strikes with sophisticated cyber operations to capture President Nicolás Maduro. This event not only ended Maduro's regime but also exemplified modern hybrid warfare, where digital disruptions amplify physical force.
Kinetic warfare formed the core of the operation. Explosions rocked Caracas and surrounding areas as US forces targeted military sites, including Fort Tiuna, using airstrikes and helicopter insertions. The rapid decapitation strategy swiftly neutralised key regime defences, leading to Maduro's capture and extradition. This traditional use of physical force, bombs, troops, and direct engagement, followed historical interventions. Power cuts observed in the region were attributed to US kinetic attacks by the Venezuelan press and the National Electric Corporation.
What set this apart was the integration of cyber warfare. President Donald Trump and Dan Caine suggested that the US used cyber capabilities to support the operation ("non‑kinetic effects" due to "a certain expertise that we have"); marking the first time a US president has acknowledged offensive capabilities against another nation. This marks one of the most public uses of US cyber power against another nation.
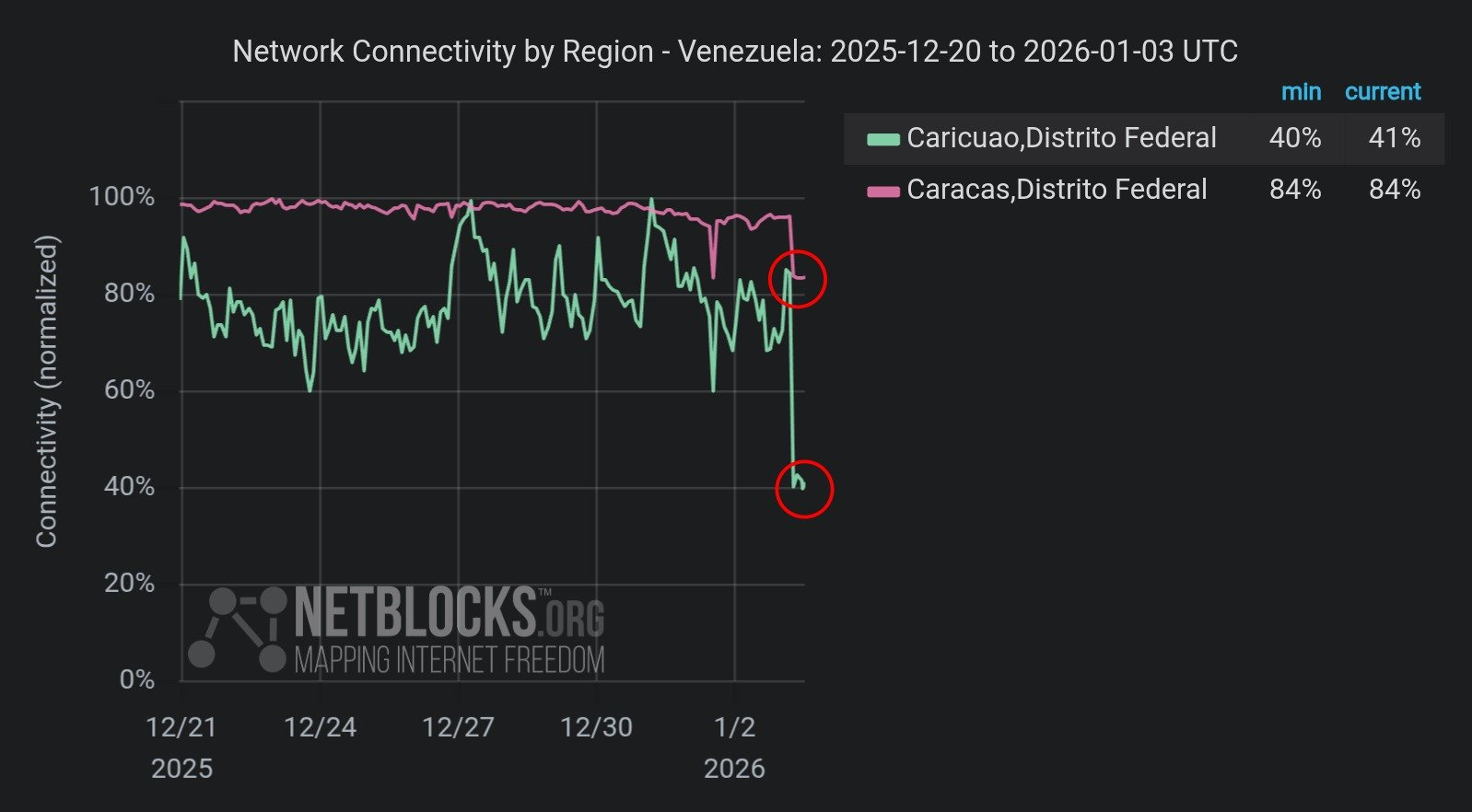
Reports and commentaries indicate US cyberattacks disrupted electricity and communications in Caracas, plunging parts of the city into darkness and hampering regime coordination. These blackouts, seemingly attributed to advanced technical capabilities, created a tactical advantage for incoming forces by blinding defences and sowing confusion. The disruption of power, air defence systems, and communication services gave the US a window of relative superiority.
Netblock was one of the first to report on the loss of internet connectivity in Caracas, aligning with the power cuts observed in the country.
Image 1. Netblocks reports on Network connectivity in the region (X, 2026)
Other sources reported that Russian-made air defence systems and Chinese-made radar systems were disrupted during the strike, obstructing the Venezuelan government’s ability to effectively respond.
This intervention highlights how cyber tools can enable kinetic success, by supporting operations and creating opportunities. Yet it raises serious questions about sovereignty, escalation, and the blurring lines in modern conflict. Namely, it raises high concern of the possibility of cyber attacks causing direct or indirect loss of life.
The Venezuela blackout and US operation shows that cyber and kinetic actions have now fully converged, from theory to practical application, with precision cyber operations against power, communications, and IT/OT/ICS infrastructure now determining outcomes before any physical force is applied. This is a reminder to Critical Infrastructure organisations that their assets must be considered as national security targets, potentially being in the scope of nation-state actors.
What we read this week
Ongoing Attacks Exploiting Critical RCE Vulnerability in Legacy D-Link DSL Routers - Researchers at The Hacker News have reported active exploitation of a critical command injection flaw, CVE-2026-0625 (CVSS 9.3), in the dnscfg.cgi endpoint of end-of-life D-Link DSL gateways. This unauthenticated vulnerability allows remote attackers to execute arbitrary shell commands, potentially leading to DNS hijacking and full router compromise. Affected models include DSL-2640B, DSL-2740R, DSL-2780B, and DSL-526B with outdated firmware, which are no longer supported and thus unpatchable. Exploitation was first observed in late November 2025, linked to DNSChanger-like behaviour that redirects or intercepts traffic. Organisations are urged to retire these legacy devices immediately, upgrade to supported models with regular updates, and monitor for altered DNS settings as indicators of compromise.
Dozens of Major Data Breaches Linked to Single Threat Actor - SecurityWeek details how an initial access broker known as 'Zestix' (alias 'Sentap') has been tied to numerous high-profile breaches since early 2025, exploiting credentials stolen via infostealers like RedLine and Lumma. The actor targets file-sharing services such as ShareFile and Nextcloud lacking MFA, exfiltrating sensitive data and selling access on underground forums. Victims include aerospace firms like Intecro Robotics, government-linked entities like Maida Health, and infrastructure providers like CRRC MA, with demands involving terabytes of data. Operations date back to 2021, but surged in 2025 with over 50 successful compromises. Defences should prioritise implementing MFA on all sensitive accounts, revoking exposed credentials, and monitoring for infostealer infections to curb this commodified cybercrime vector.
FCC Proposes New Cybersecurity Rules for Telecoms Amid Salt Typhoon Breaches - Dark Reading covers the US Federal Communications Commission's proposal for enhanced network security mandates following intrusions by the Chinese-linked Salt Typhoon group, which compromised carriers like Verizon and AT&T in late 2025. The rules require telecoms to secure against unlawful access, submit annual certifications on cybersecurity risk management plans, and modernise infrastructure. Motivated by escalating threats to national security, the framework emphasises resilience and aligns with guidance from CISA and NSA on patching and hardening. Affected carriers face immediate compliance if adopted, with implications for broader supply chain security. Telecom organisations are advised to prioritise vulnerability management, incident response, and collaboration with federal agencies to mitigate state-sponsored risks.
Rising AI Skepticism in Cybersecurity as Hype Meets Reality - A Dark Reading analysis explores growing doubts about AI's role in cybersecurity, driven by unmet ROI from generative AI pilots, high costs, and misuse by threat actors in 2025. Despite widespread adoption, only half of organisations report benefits, with critics highlighting 'AI washing' by vendors and unsustainable infrastructure investments akin to past bubbles. Recent developments include stock dips and failed implementations lacking clear use cases, while threats like AI-powered ransomware claims are debunked. Looking to 2026, experts predict spending pullbacks but enduring value in niche areas like vulnerability patching. Defences should focus on behavioural analytics and defined AI applications, avoiding overreliance on unproven tools.
UK Launches New Cyber Unit to Bolster Defences Against Evolving Threats - Infosecurity Magazine reports on the UK's £210 million Government Cyber Action Plan, announced on 6 January 2026, which establishes a central Cyber Unit led by the national CISO to enhance risk identification, incident response, and recovery across public services. Driven by increasing attacks disrupting digital infrastructure, the plan mandates government departments to meet the same standards as critical operators, supporting digitisation goals worth £45 billion in savings. Coinciding with the Cyber Security and Resilience Bill's second reading, it addresses sophisticated threats through coordinated monitoring and robust protocols. Public sector organisations are encouraged to integrate these measures swiftly, ensuring faster threat mitigation and resilience building.
Referenceshttps://thehackernews.com/2026/01/active-exploitation-hits-legacy-d-link.htmlhttps://www.securityweek.com/dozens-of-major-data-breaches-linked-to-single-threat-actorhttps://www.darkreading.com/cyberattacks-data-breaches/fcc-new-cybersecurity-rules-telecomshttps://www.darkreading.com/cybersecurity-operations/contrarians-no-more-ai-skepticismhttps://www.infosecurity-magazine.com/news/uk-launches-new-cyber-unit/