Sentap: Data Leaks, Initial Access and Extortions
“Sentap”: Data Leaks, Initial Access and Extortions
NSB Cyber is closely tracking the following threat, analysing dark web activity and collaborating with industry partners to validate the claim and assess potential exposure. We will provide updates as new information emerges. For assistance with incident response, monitoring and risk assessment, contact our team through intelligence@nsbcyber.com.
TLDR
Sentap (sentap.cyber) has recently increased global operations and targeted Australian entities including NBN Co and Urban-X through data extortion and initial access operations. Recent Australian breaches include the theft of over 300GB of infrastructure and PII data from NBN Co, indicating the potential for widespread operational impact.
The actor exploits misconfigured internet-facing assets, compromised accounts and third-party access to exfiltrate sensitive data, later extorting victims via encrypted communication channels.
Sentap is believed to be an active participant in FunkSec’s Ransomware-as-a-Service (Raas) and data broker operations, with activity spanning global targets and forum-based distribution.
NSB Cyber suggests to organisations to assess external exposure, enforce MFA, secure file-sharing infrastructure, monitor for leaked employee and third-party supplier credentials, and implement IP Allow-listing and DLP controls.
Figure 1. Sentap Threat Mappings
Snapshot
The NSB Cyber Intelligence Center (CIC) is reporting on an emerging threat actor Sentap (sentap.cyber) which the NSB CIC has been tracking for a few months. The Threat Actor has targeted multiple Australian organisations, including the Telecommunications and broadband network provider provider NBN Co, and real estate consultant company Urban-X (urbanx.io).
The Threat Actor is assessed to be motivated by financial gain, with ties to Ransomware group FunkSec. Sentap has been observed communicating in English and Russian on multiple different platforms.
This advisory is aimed at all organisations, regardless of sector, who should review their security controls to reduce the risk. NSB Cyber suggests to organisation to assess their exposure to the threat and implement the following recommendations.
Targeting and Impact
Sentap AKA sentap.cyber, who specialises in establishing Initial Access (Initial Access Broker) and data extortion, has been targeting organisations globally across multiple verticals since at least 2021. In 2025, the Threat Actor has increase its operations and activity on data breach forums. Previously targeted countries by the group include but not limited to Australia, France, Italy, Germany, India, United States, Canada, UAE, Kenya, Malaysia and Brazil. Sentap appears to be financially motivated, focusing on opportunistic attacks or low hanging fruit operations.
The Threat Actor has been observed publishing on data leak forums, including BreachForums (Defunct), DarkForums, Raidforums (Defunct), XSS, and Exploit — at least on a weekly and/or fortnightly basis. Sentap’s posts appear to receive minimal, or low-level traction. However, it may be an indicator that potential buyers are reaching out directly to the Threat Actor through encrypted and private messaging platforms. Commonly used platforms by the Sentap include Telegram, the Jabber messaging protocol, and proton mail infrastructure.
The persona Sentap has been around since 2021 where posts selling access, data leaks and hacking resources would be provided by the Threat Actor. The Threat Actor is assessed to be of moderate sophistication, leveraging AI for communications with victims and other malicious actors. The Threat Actor engages in opportunistic operations and employs a non-aggressive communication style with victims. Our analysis indicates that the primary focus is data exfiltration, followed by demanding payment to prevent data release or selling the stolen data to third parties.
On June 5, 2025, Threat Actor Sentap listed a 306GB dataset for sale from NBN Co Queensland, Australia’s national broadband network. This data included specific critical infrastructure information from Fibre to the Curb (FTTC) and Hybrid-Coaxial (HFC) projects in Queensland, as well as blueprint, bore lag, personally identifiable information, and other optimisation project plans.
Figure 2. Sentap advertise data from NBN Co on Darkforums
Figure 3. Sentap advertise the data of Urban X on XSS Forum
Evidence found by NSB CIC, and multiple other sources, seems to indicate that Sentap is part of the broader ransomware group FunkSec. An interview with FunkSec acknowledged inclusion of Sentap as a member alongside Scorpion, MRZ, and el farado (https://osint10x.com/threat-actor-interview-spotlighting-on-funksec-ransomware-group/). Sentap has been denoted to have forum operator title, which allows him to operate and moderate the FunkSec forum, and appears to also manage activities on the FunkBID site, which was initially reported by Bitdefender in March 2025. The Threat Actor has also been observed making multiple social media posts in reaction to FunkSec impersonators, or other FunkSec operations. The Threat Actor also possess a keybase account with direct links to other FunkSec members.
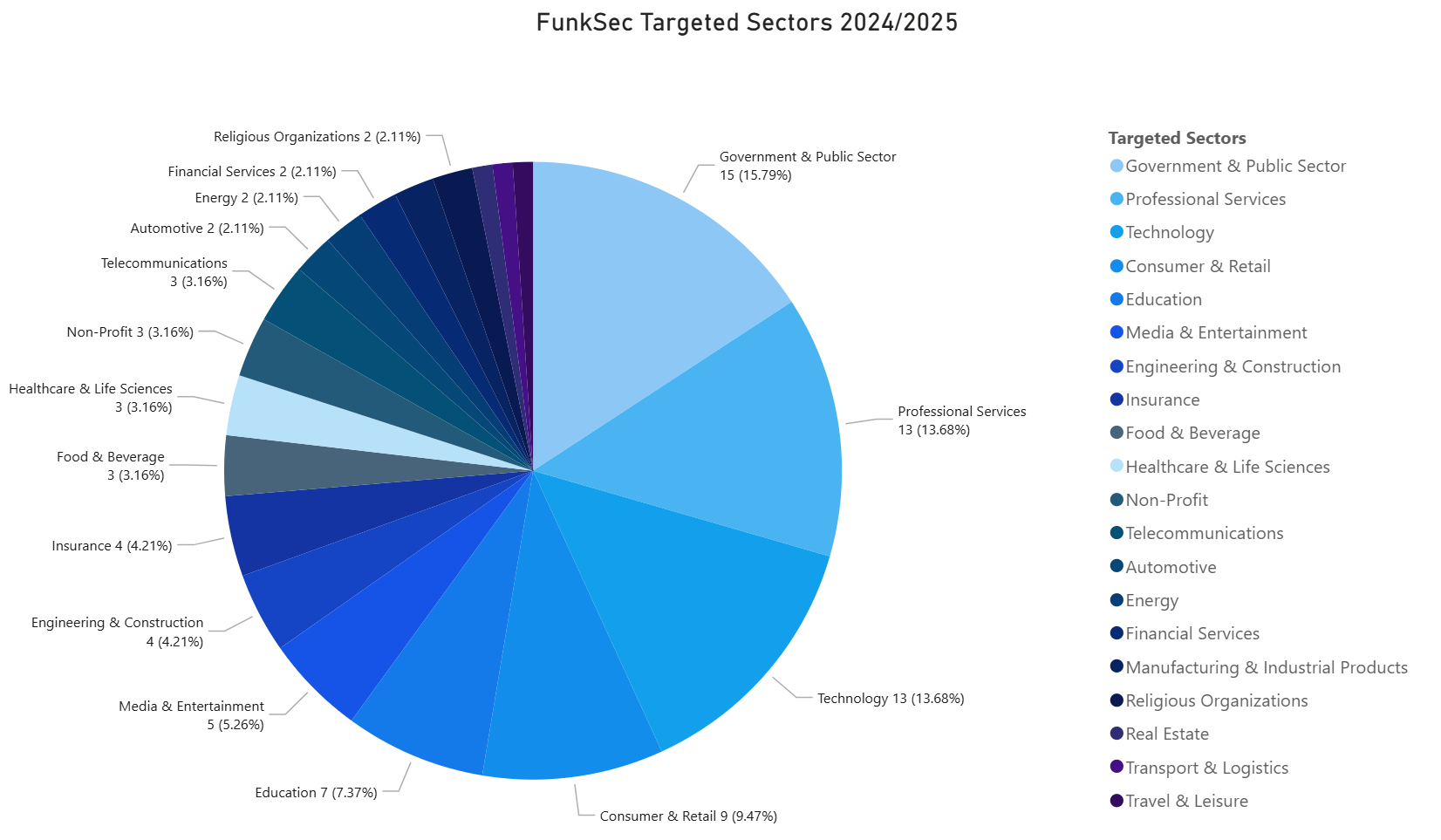
Active since 2024, FunkSec operates as an initial Access Broker, Data Broker and Ransomware-as-a-Service operation. They has been gaining attention rapidly. Their large number of victims (~170) globally, re-victimisation, and use of AI in operation and for malware building have made them a threat worth monitoring and mentioning. According to Check Point researchers, the groups presents a lack of technical expertise which would have been compensated by the use of AI, especially to develop their malware codebase. Whilst these actors understand how programming work, they lack the capabilities to develop and code their tools themselves. However, the use of AI has allowed the group to sell their services, perform multiple operations and gain notoriety within current threat actors.
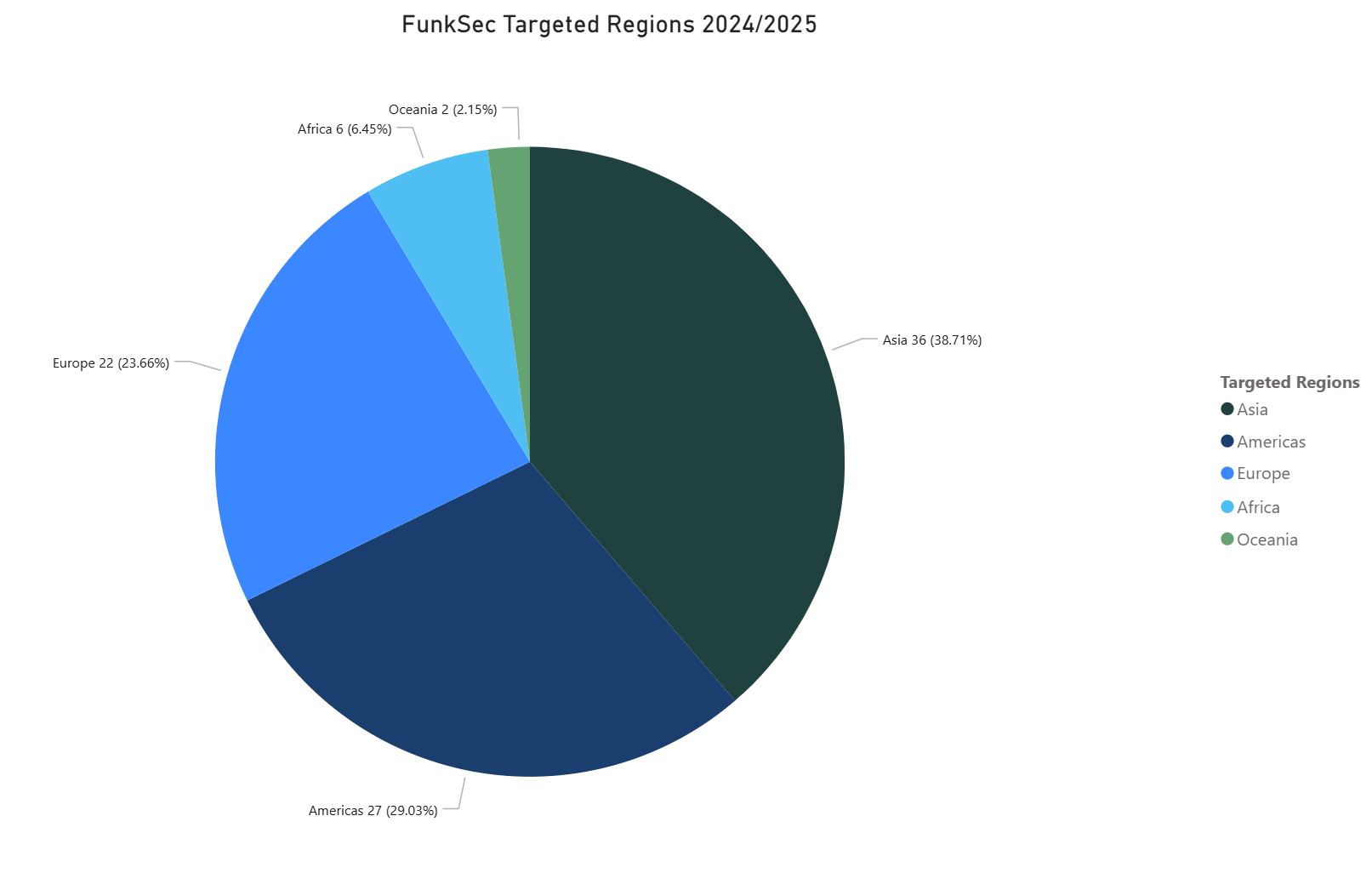
The group appears to have been inactive since March 2025 — exemplified by a lack of recent publications and their TOR leak site being offline. However, prior to to this, the group has been targeting key industries such as Government and Public Sector, Technology, Professional Services, Consumer and Retail, and Education. Their most targeted countries are United States, India, Spain and Mongolia. Whilst the group affirms to not be politically affiliated/motivated, their operations seems to be likely motivated by an anti-sentiment against Israel and the United States. Their financial approach adopts a method of “spray-and-pray”, where the group is paid little and often, rather than going after high-profile targets for large amounts.
FunkSec has been observed to attempting to associate their actions with defunct groups such as Ghost Algeria and Cyb3r Fl00d. These connections probably reflect efforts to enhance FunkSec’s reputation by associating with prominent names, rather than signifying actual membership or partnership. The group has also been previously criticised for recycling data sets from previous campaigns.
Figure 6.0 Sentap’s “X” post regarding potential FunkSec impersonators
Whilst Sentap appears to have involvement in operations undertaken by the group, recent data leak publications appears to be separate and distinct operations.
NSB Cyber assess with moderate to high confidence that the Threat Actor may target Australian organisations in the future. As the threat has targeted Australian entities in the past, organisations are advised to review and implement recommended security controls.
Attack Vector & Overview
NSB Cyber’s CIC has observed Sentap leveraging compromised accounts and leaked credentials to access infrastructures. The Threat Actor was also observed interacting with Initial Access Brokers to gain access to victim environments.
It is assessed that Sentap also hunts for poorly configured and public-facing instances, such as Open-Ports, Cloud platforms, and VPNs, for points of entry and vulnerabilities. Numerous publications on forums regarding potential exploits and enquiries regarding port exploitation appear to suggest a moderate level of sophistication.
In a specific operation seen by NSB CIC, the Threat Actor leveraged Valid Accounts: Cloud Accounts [T1078.004] and abused a trusted relationship to gain access to its target by a third-party [T1199]. In this context, the Threat Actor compromised an account belonging to a third-party.
The Threat Actor was then able to access its targets’ file sharing infrastructure and established a connection through a third-party SFTP application to exfiltrate the data hosted [T1540/T1048]. This allowed Sentap to exfiltrate all files accessible from the third-party account over a period of more than 30 hours.
The Threat Actor then left ransom notes within the organisation’s file sharing infrastructure and made posts on data leak forums. Follow these actions, the Threat Actor, was observed leveraging proton mail (sentap[.]cyber@proton[.]me) to communicate with its victims, requesting for an urgent payment against the release of data.
Discovered Indicators of Compromise by the NSB Cyber CIC and broader reporting of the community can be found in sections Indicators of Compromise and Tactics, Techniques and Procedures below.
Mitigations and Recommended Actions
To mitigate the threat posed by Sentap and other opportunistic data leak Threat Actors, organisations and individuals should implement the following security measures:
1. Assess and limit exposure of internet-facing assets: Review and evaluate the exposure of all publicly-facing assets, potentially isolating business-critical systems and identifying vulnerabilities that could be exploited by threat actors. Threat actors such as Sentap have been observed scanning for open ports and accessible vulnerable devices or infrastructure that could be leveraged to gain access to your environment. This includes, but is not limited to, open ports, VPNs, routers, and firewalls.
2. Secure file-sharing infrastructure: Evaluate and strengthen file-sharing infrastructure by implementing robust security configurations to prevent unauthorised access or data exfiltration. Key actions include:
a. Implement a user access review (UAR) process for management to review user access on a defined frequency to disable unnecessary internal and external accounts.
b. Monitor and enforce Download/Upload limit for non-privileged users. This prevents unauthorised users, and privileged users from exfiltrating (or uploading) large amount of data from organisational infrastructure.
c. Disable or Secure other unused file-sharing protocols to ensure connections to the platform are limited to specific methods, especially if not required for business operations . For example, disable SFTP and FTP access to the platform, including other external tools leveraging non-web portal access, to prevent large quantity of file exfiltration/download.
3. Enforce network access control policies (IP Allow-listing): Implement access control policies, such as device-based or IP-based allow-listing, to restrict access to business-critical assets. These policies help prevent unauthorised access from compromised accounts by granting or denying access based on predefined criteria, significantly reducing the risk of exploitation by malicious actors.
4. Monitor for leaked credentials and compromised accounts: Deploy advanced monitoring tools, such as those provided by NSB Cyber, to detect leaked credentials and compromised accounts across domains, sub-domains, and related infrastructure. Proactive monitoring helps reduce the attack surface by identifying and mitigating vulnerabilities before they can be exploited by threat actors. This monitoring should also seek to include third-party suppliers that have access to organisational infrastructure.
5. Enable multi-factor authentication on all perimeter technologies: Implement multi-factor authentication (MFA) across all perimeter technologies to provide an additional layer of security against password-based attacks and credential theft. Threat actors, including Sentap and FunkSec, have been known to exploit leaked credentials through techniques like credential stuffing, making MFA critical for protecting infrastructure.
6. Implement third-part auditing for any external accounts: Mandate independent, periodic audits for all third parties with access to client environments, focusing on access control hygiene. These audits should evaluate account ownership, verify the necessity of access, and ensure alignment with the principle of least privilege to minimise potential risks from external accounts.
7. Review and Implement DLP (Data Loss Prevention) policies: Ensure DLP policies are in place and regularly reviewed to prevent unauthorised sharing, downloading, or transfer of sensitive information via file sharing infrastructures. Policies should align with data classification levels and include controls such as content inspection, real-time alerts, and automatic enforcement actions.
Prior to considering active configuration changes within your environment, please take into account current configurations and environmental security controls.
External References:
https://www.watchguard.com/wgrd-security-hub/ransomware-tracker/funksec/
https://osint10x.com/threat-actor-interview-spotlighting-on-funksec-ransomware-group/
https://research.checkpoint.com/2025/funksec-alleged-top-ransomware-group-powered-by-ai/
https://www.cyfirma.com/news/weekly-intelligence-report-09-may-2025/
https://www.cyberdaily.au/security/11575-inside-funksec-the-self-taught-hackers-supported-by-ai-code
DISCLAIMER
This threat advisory is based on information gathered from open and closed sources by NSB Cyber’s analysts, and has been curated and analysed to ensure the information provided is accurate and provided without legal guarantee. Readers are advised by NSB Cyber to take into account current configurations and environmental security controls prior to considering active configuration changes within their corporate environment.
Indicators of Compromise
| Indicator | Type | Description |
|---|---|---|
| bc1qtc6d8gvaru0r4ang7ltuu77aaz9pr8vx4h5372 | Cryptocurrency address | Bitcoin address |
| t1ZhQu6pJkZcUJ3f5rWYUFFgSUvVQDN1H8e | Cryptocurrency address | Zcash-T address |
| 86RyWuuewTfN36v4hNLREw9NsghS4BvNJ3UX724KWw5L6kid719yVAYA8b8pM8GrDrKpT5CZspGa2GpmEE2Zkijo3ArvZwY | Cryptocurrency address | Monero address on DarkForums |
| sentap[.]cyber@proton[.]me | Address email used in operations | |
| sentap@jabber[.]fr | Address email used in operations (XMPP/Jabber ID) | |
| sentap@creep[.]im | Address email used in operations (XMPP/Jabber IDs) | |
| 146[.]70[.]28[.]158 | IPv4 | IP used by Threat Actor in operations |
| 185[.]38[.]142[.]157 | IPv4 | IP used by Threat Actor in operations |
| 103[.]225[.]130[.]95 | IPv4 | IP used by Threat Actor in operations |
Tactics, Techniques and Procedures
| Tactic | Technique/Sub-Technique | Description |
|---|---|---|
| TA0001: Initial Access | T1078.004: Valid Accounts: Cloud Accounts | Valid accounts in cloud environments may allow adversaries to perform actions to achieve Initial Access, Persistence, Privilege Escalation, or Defense Evasion. Cloud accounts are those created and configured by an organisation for use by users, remote support, services, or for administration of resources within a cloud service provider or SaaS application. Cloud Accounts can exist solely in the cloud; alternatively, they may be hybrid-joined between on-premises systems and the cloud through syncing or federation with other identity sources such as Windows Active Directory. |
| TA0001: Initial Access | T1199: Trusted Relationship | Adversaries may breach or otherwise leverage organisations who have access to intended victims. Access through trusted third party relationship abuses an existing connection that may not be protected or receives less scrutiny than standard mechanisms of gaining access to a network. |
| TA0009: Collection | T1530: Data from Cloud Storage | Adversaries may access data from cloud storage. |
| TA0010: Exfiltration | T1048: Exfiltration Over Alternative Protocol | Adversaries may steal data by exfiltrating it over a different protocol than that of the existing command and control channel. The data may also be sent to an alternate network location from the main command and control server. Alternate protocols include FTP, SMTP, HTTP/S, DNS, SMB, or any other network protocol not being used as the main command and control channel. Adversaries may also opt to encrypt and/or obfuscate these alternate channels. |